Cloud computing has become the backbone of modern organizations. The widespread use is due to standout benefits such as flexibility, scalability, faster time-to-market, advanced security, and more. According to recent stats, the cloud computing market size was valued at $1125.9B in 2024 and is expected to grow from $1294.9B in 2025 to $2281.1B by 2030.
Considering the buzz and global adoption of cloud, security risks and threat actors don’t stay behind. Well, cloud security challenges are a significant concern that can lead to highly disruptive consequences. Organizations are exposed to attacks because they fail to implement appropriate security practices and neglect their responsibilities.
That being said, in this blog, we will look at the top 5 cloud computing security challenges organizations face. Before we get to the main topic, let’s understand cloud security in short.
An Overview of Cloud Security
Cloud security or cloud computing security is defined as the set of processes, rules, and technologies to keep your data, applications, and systems that are hosted on the cloud secure.
In addition, it ensures that only authorized users can access sensitive information while maintaining regulatory compliance. Cloud security can work according to the company’s specific requirements, including access controls, traffic monitoring, and more.
With centrally managed, customizable security controls, organizations can reduce administrative effort, lower costs, and allow IT teams to focus on their core business goals. With the increasing complexity of the cloud environment, cloud security has become the top priority for preventing breaches, reducing risk, and ensuring business continuity.
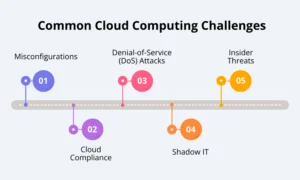
Common Cloud Computing Security Challenges Explained
Cloud computing poses several security challenges due to its distributed nature, resource sharing, and reliance on third-party providers. Here’s a rundown of the top 5 challenges you need to know.
1] Misconfigurations
There are several reasons why cloud security misconfiguration occurs:
Because cloud platforms are optimized for data sharing and accessibility, it becomes difficult for security professionals to ensure only authorized users can access the data.
The next is that organizations use many CSPs, each having its own set of security implementations and settings, making it difficult to understand each of these. It can also lead to misconfiguration in the system, which hackers can easily exploit.
2] Cloud Compliance
Organizations need to comply with regulations such as PCI DSS and HIPAA to protect sensitive data. This includes important personal details, financial records, credit card numbers, and more.
Meeting these regulatory requirements becomes challenging in cloud environments where data is distributed across multiple systems. Restrictions are imposed on access and on what individuals with access can do, while ensuring compliance with the standards.
In the absence of effective identity and access management (IAM) systems, persistent monitoring organizations find it challenging to track network access, identify unauthorized access, and ensure cloud compliance, thereby creating a significant security problem.
3] Denial-of-Service (DoS) Attacks
DoS attacks can overwhelm the system with constant traffic, making the system crash or shut down completely. This stands as a significant cloud computing security issue. Alongside network downtime, revenue losses can impact overall company credibility and customer satisfaction. Cloud experts need to be ace at implementing and mitigating strategies for DoS attacks.
In 2020, Amazon Web Services (AWS) suffered a distributed denial-of-service (DDoS) attack that impacted many customers.
4] Shadow IT
Shadow IT has become a growing concern in the cloud today. It’s about using devices, software, and apps without IT approval. With the growing demand for and use of cloud services, Shadow IT allows employees to deploy cloud-based apps that the IT team isn’t aware of.
Security policies can be bypassed when employees use unapproved tools, leading to increased data leakage and unauthorized access. Shadow IT also complicates organizations’ efforts to implement data privacy requirements and regulatory compliance.
5] Insider Threats
Insider threats are the most common security issues within organizations. Alongside that, it’s often overlooked by many. It means authorized users, or employees here, may intentionally abuse or reveal sensitive information, including customer data, financial records, medical information, and other sensitive information.
These types of sensitive data may put customers at risk and erode trust in the company. Such risks are not just mistakes; it’s all about a lack of vigilance over security or a casual attitude to the information.
Organizational access controls, security awareness, and continuous cloud activity monitoring should be enforced to minimize insider-related incidents.
Wrapping it Up!
Here we come to the end! Hope you now have an idea about the top cloud computing security challenges that need to be effectively addressed. Cloud computing is on its way to expand and offers limitless possibilities; however, security won’t be left behind. Cloud security challenges are an essential concern for organizations worldwide.
It’s necessary to stay vigilant, incorporate the best security practices, restrict access controls, follow the cloud compliance regulations, and more to stay ahead of the cyberattacks and attain business success using a cloud environment.
Check out our website to stay in the loop on more trending blog updates.
FAQs
1. What are the 4 Cs of cloud computing?
Answer: The 4 Cs of cloud computing are: Code, Container, Cluster, and Cloud.
2. Which are the 5 pillars of cloud security?
Answer: The five pillars of cloud computing security are: Identity & Access Management (IAM), Network Security, Data Security, Compliance & Governance, and Incident Response.
Recommended For You:
Advantages of Cloud Computing for Businesses: Surpassing the Competition