In today’s world, with the rise in technology, there is a high probability of loss of your valuable data and a chance of a cyber-attack too.
Seeing such risk companies tend to enhance their cybersecurity programs and here comes the role of Managed Security Service Provider (MSSP). Most likely a layman can get confused between MSSP and MSP (Managed Service Provider).
In this blog, we will look at the differences between a Managed Security Service Provider and a Managed Service Provider, i.e. MSSP vs MSP but first, let us know about them briefly.
What is MSSP?
MSSP stands out as a Managed Security Service Provider. This type of company mainly focuses on security risks (more or fewer cybersecurity risks that can affect your networking systems).
The main aim of such companies is to assess the risks and provide some remedies and solutions to tackle a sudden cyber-attack.
MSSP also helps in implementing new complex security procedures and makes sure that all the employees and administration-related data are protected from breaches in cybersecurity.
What is MSP?
MSP stands for Managed Service Provider. This type of company is usually an IT service provider company that focuses on providing servers and specialized applications to users.
MSP handles all the IT administration work for other companies starting from maintenance, help desk support, bug fixes, application updates, IT support, and much more.
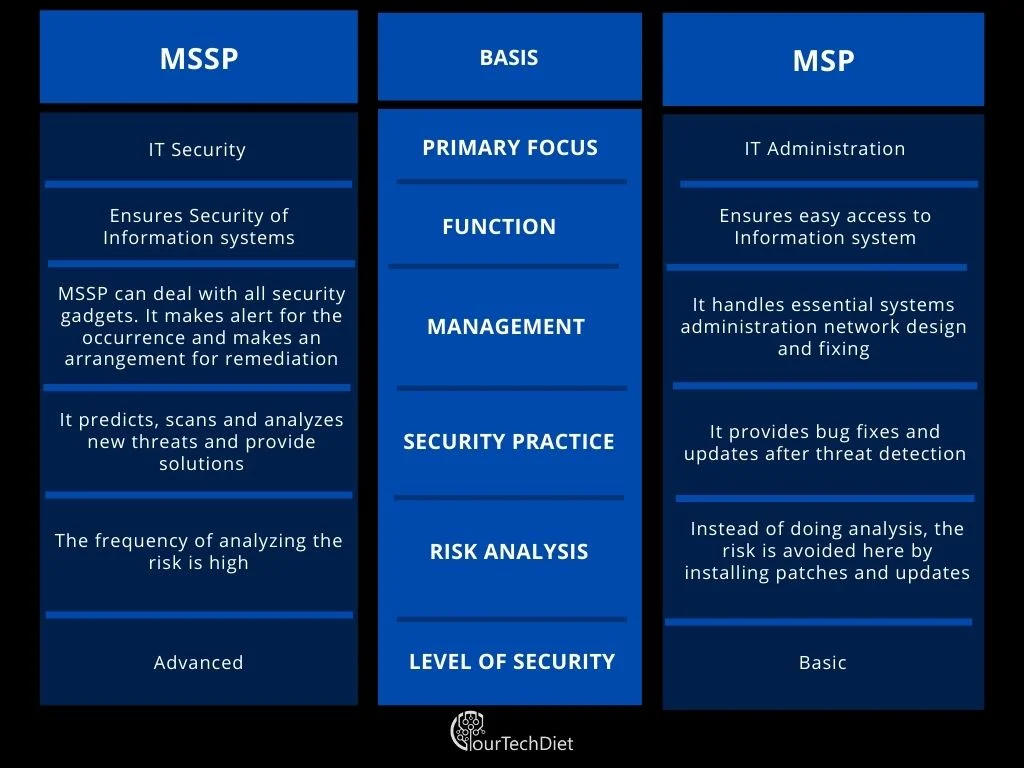
Difference between a Managed Security Service Provider and a Managed Service Provider (MSSP vs MSP):
While they both cover a part of security there are some real contrasts between the two kinds of service providers:
Conclusion:
To maintain adequate security postures, it is necessary to encompass both network and security device management using different springboards leap like a managed service provider and managed security service provider.
Recommended For You:
Best Cybersecurity Practices to Keep Your Data Safe Beyond the Holidays
Phishing: Are you really able to recognize a phishing attempt?